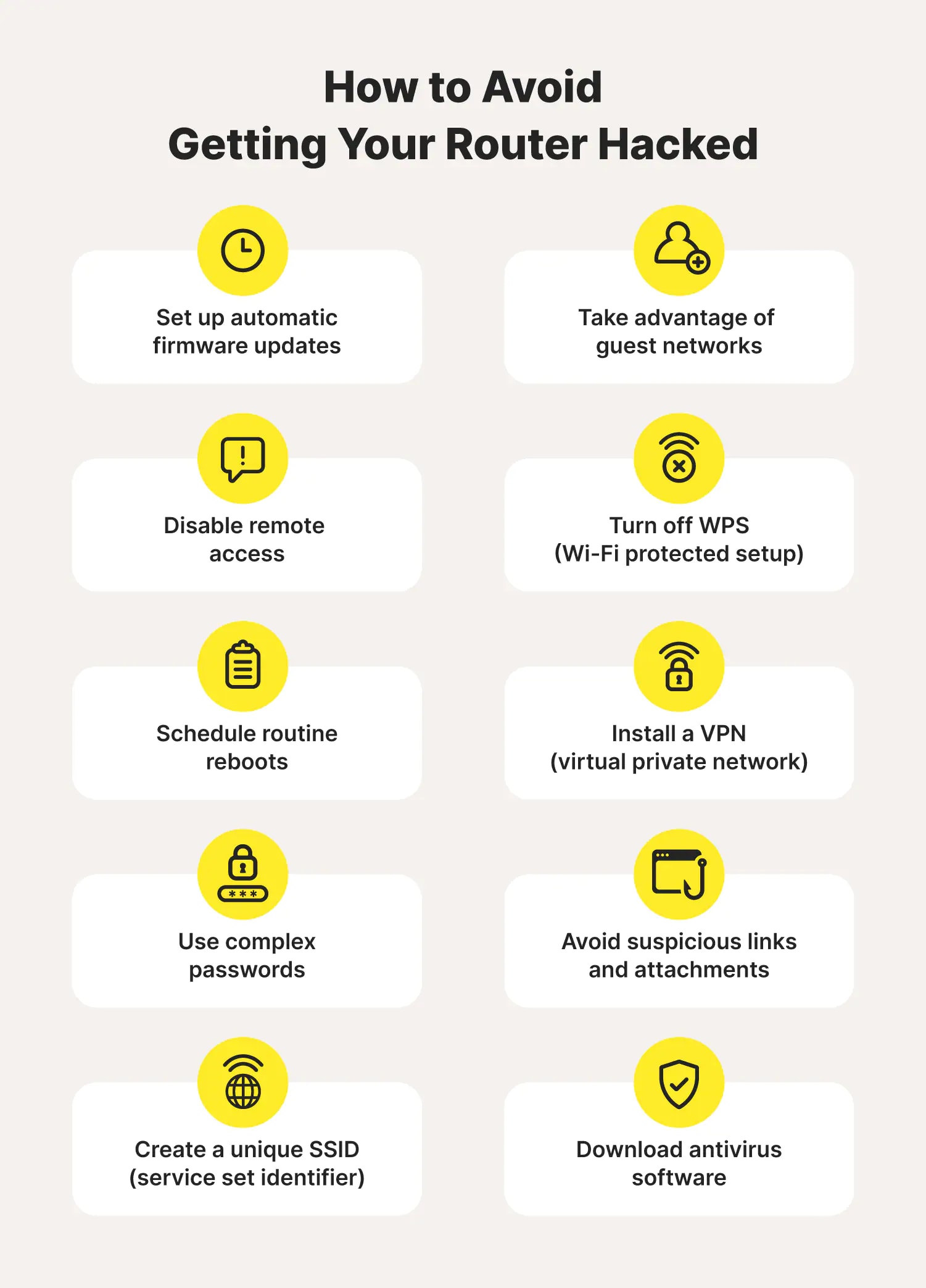
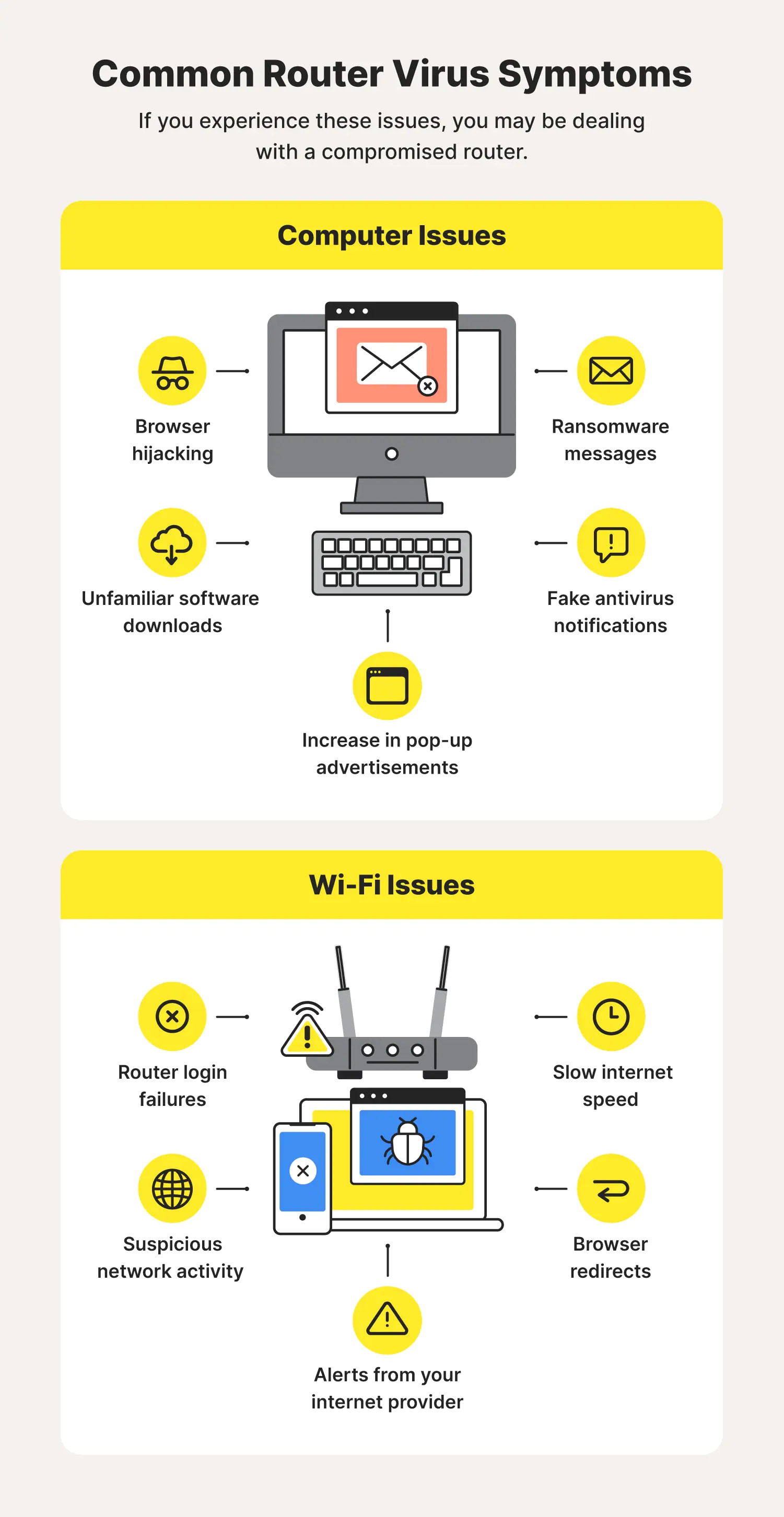
Lock Unlock Security On A Computer. Protecting The Internet Connection Through A Wi-fi Router Is A Concept Of A Security Breach. Cyber Security Stock Photo, Picture and Royalty Free Image. Image 95187003.

Lock unlock security on a computer. Protecting the Internet connection through a wi-fi router is a concept of a security breach. Cyber security Stock Photo - Alamy