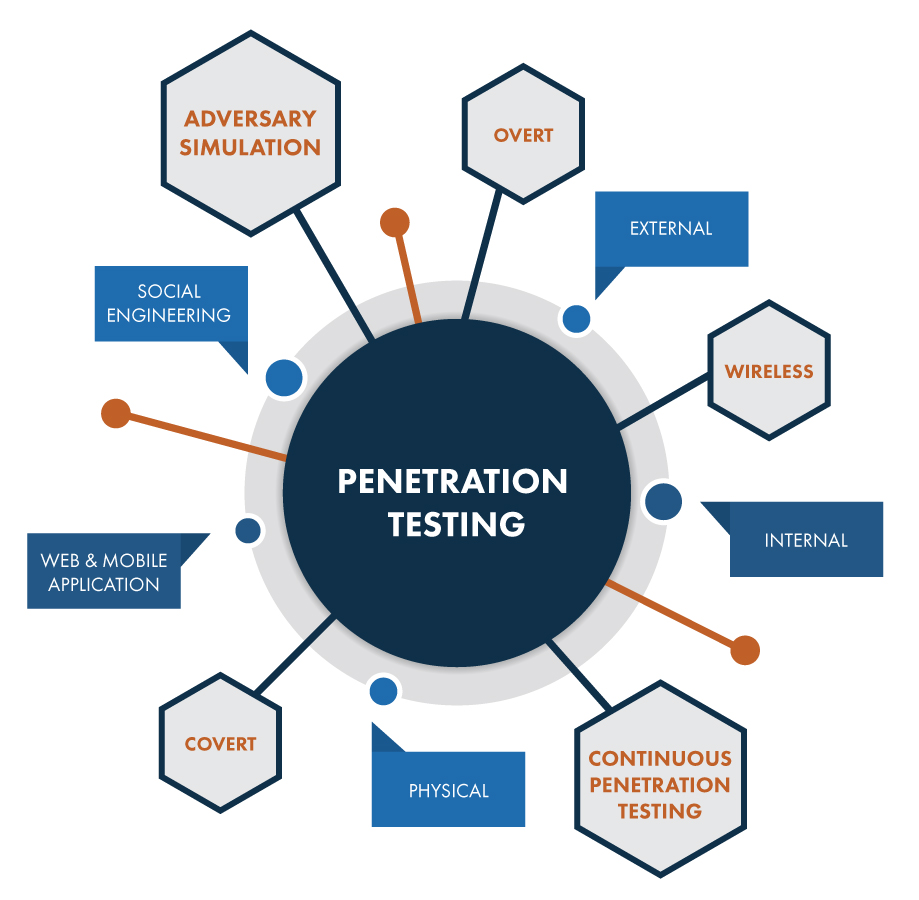
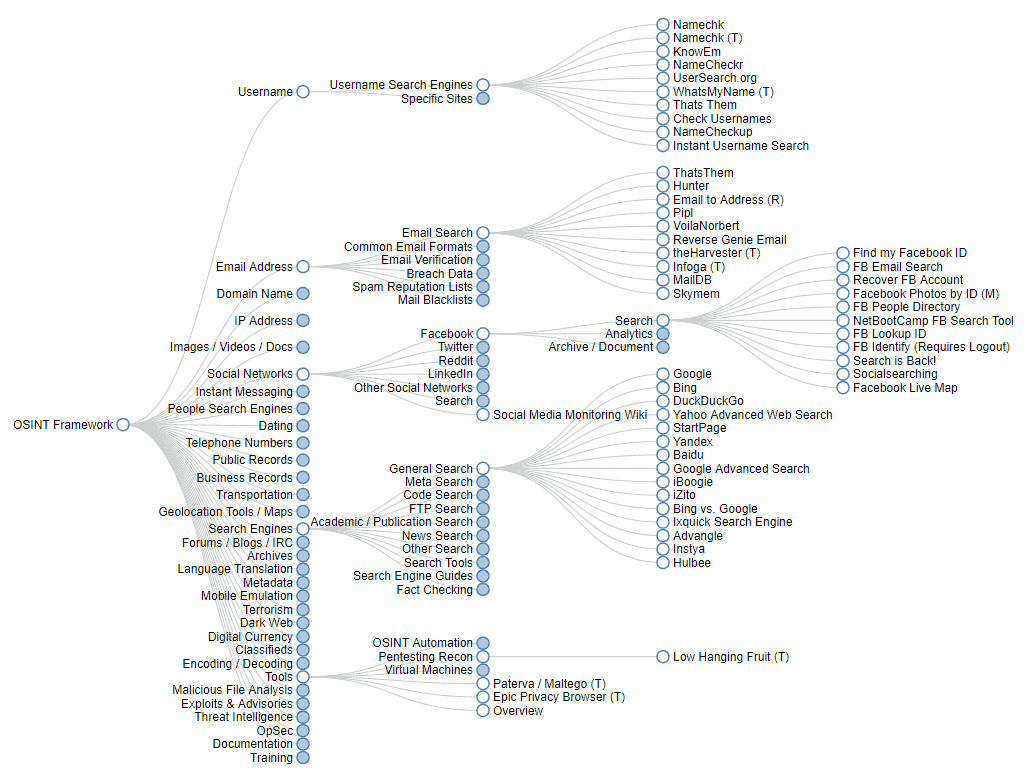
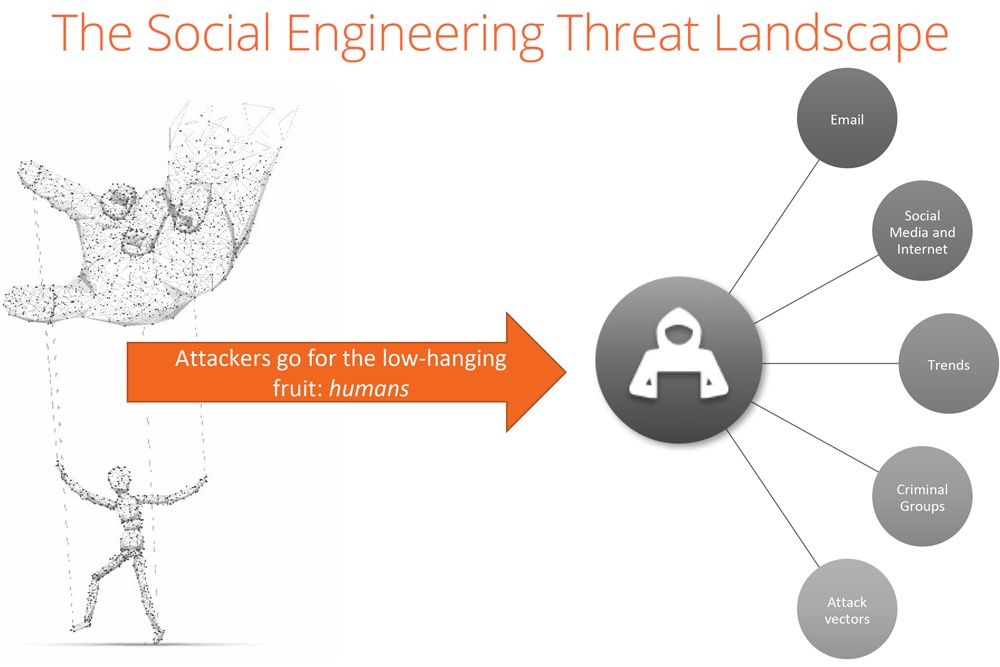
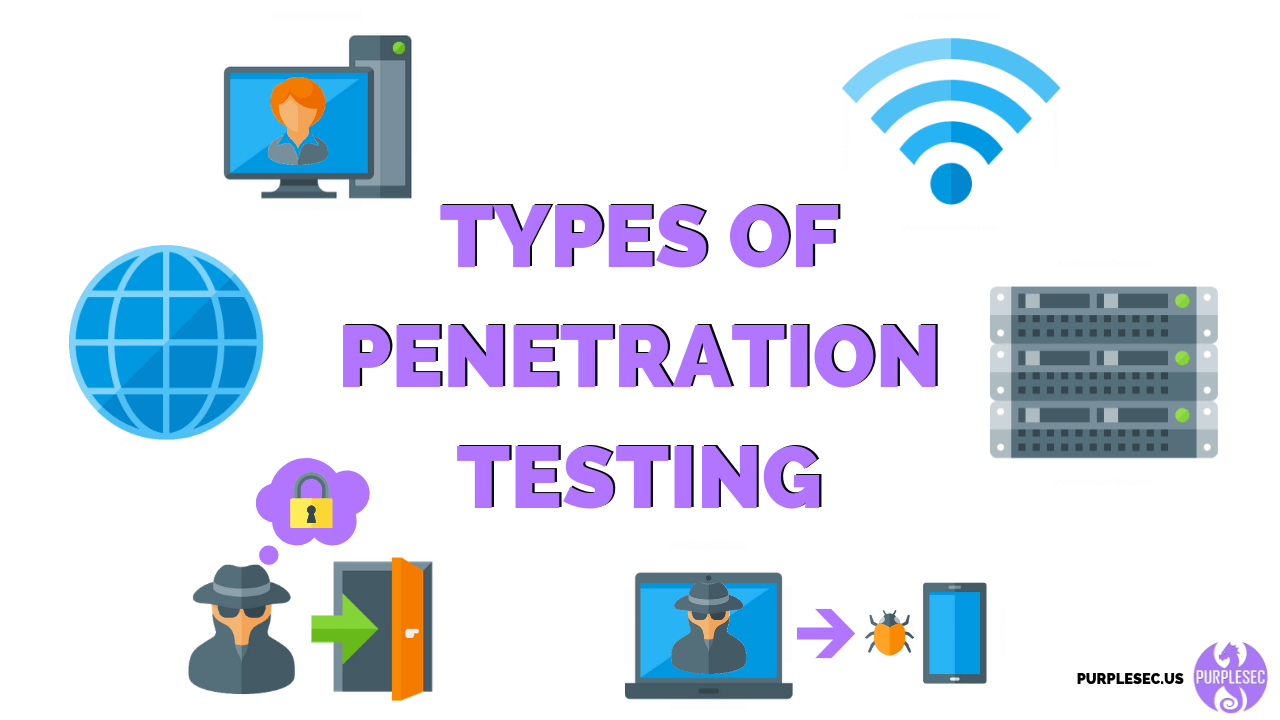
Social Engineering Penetration Testing | Managed IT Services and Cyber Security Services Company - Teceze

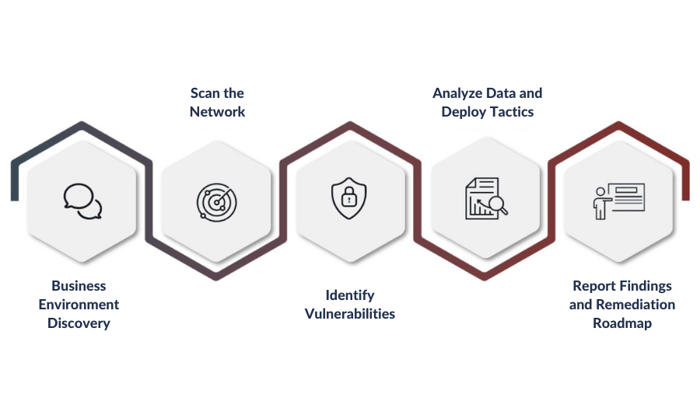
Steps of social engineering penetration testing | Mastering Machine Learning for Penetration Testing

Social Engineering Penetration Testing: Executing Social Engineering Pen Tests, Assessments and Defense: 9780124201248: Computer Science Books @ Amazon.com

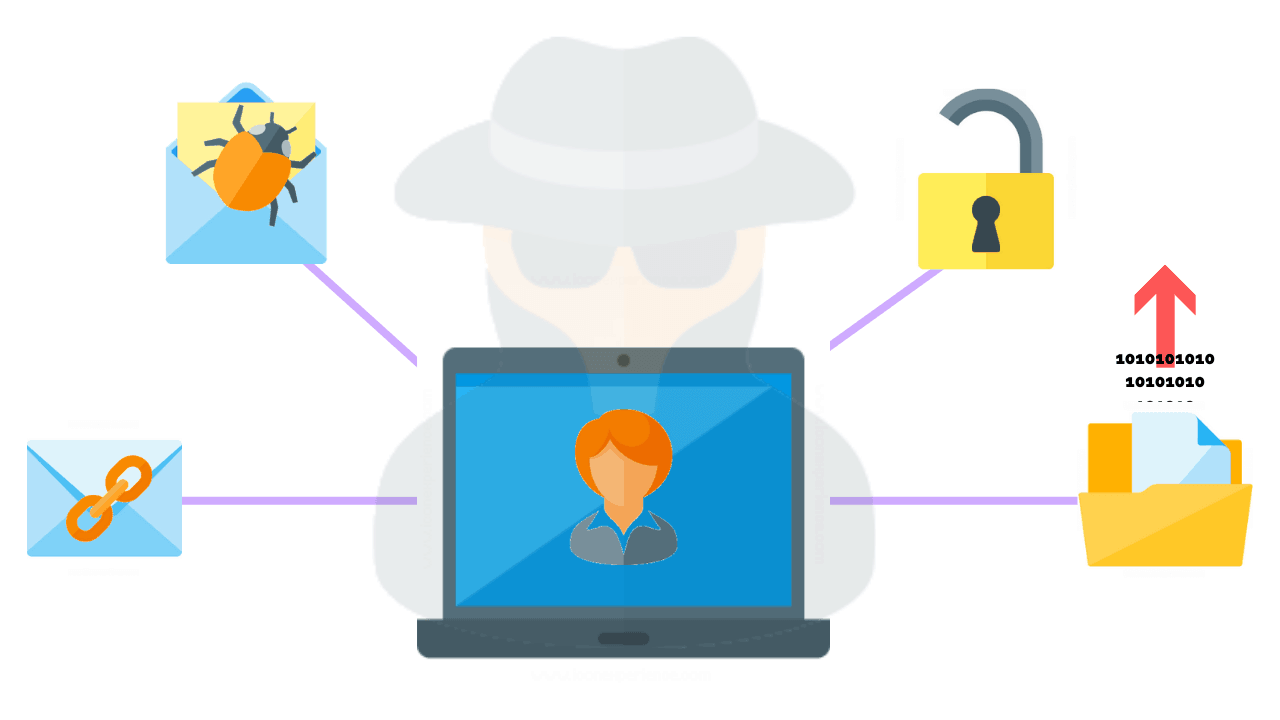
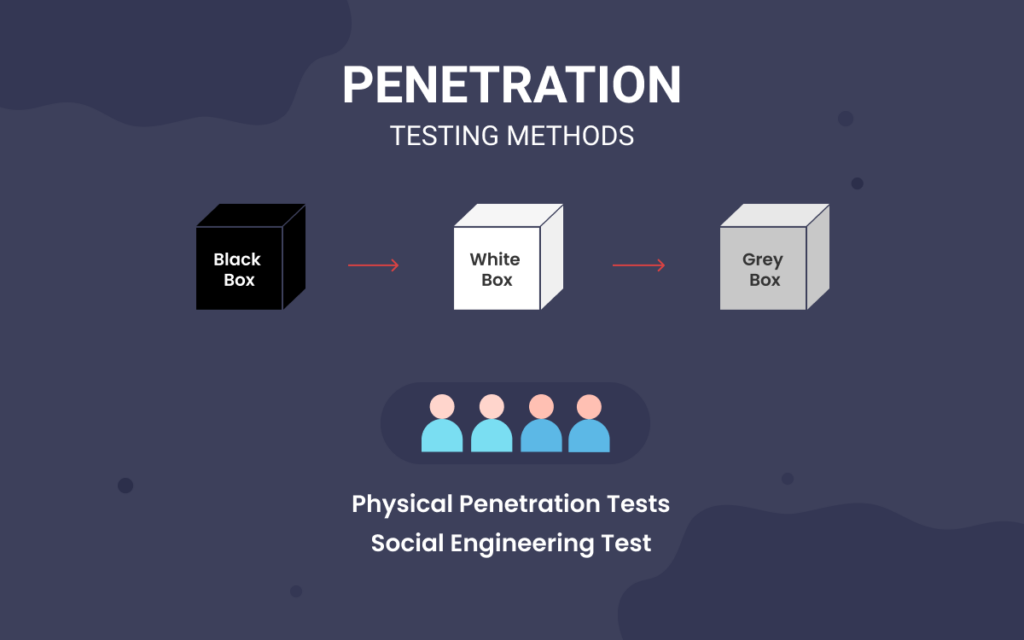
What Social Engineering Testing Is and How it Enhances Regular Penetration Testing to Simulate a Sophisticated Malicious Actor